MeasureRISK
Threat
Why Threat Modeling Matters—and Why You Need an External Perspective
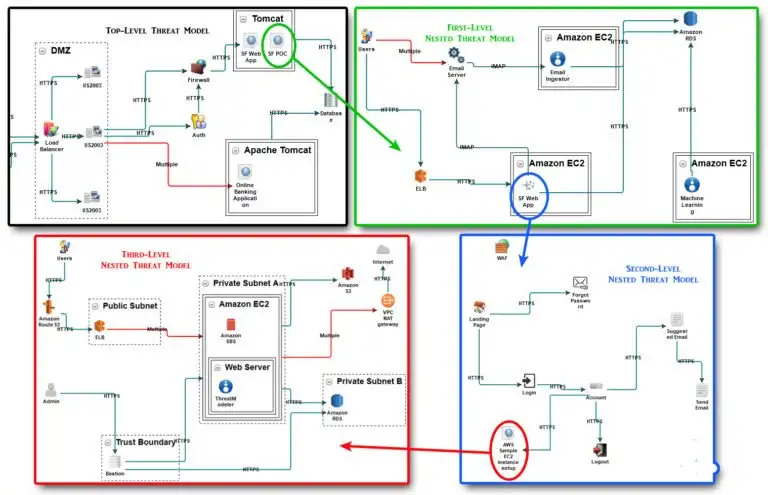
Threat modeling is more than a checklist—it’s a proactive, structured approach to understanding how attackers think. It identifies who might target you, how they could strike, and which assets they value most. This process answers essential security questions:
- Where are our most critical assets?
- Which vulnerabilities are most likely to be exploited?
- What threats are most relevant to our environment?
- Are there attack paths we haven’t considered?
We all practice informal threat modeling every day—drivers anticipate hazards to avoid collisions, and kids strategize to steer clear of playground bullies. In the same way, organizations must anticipate and mitigate risks before adversaries exploit them.
But here’s the challenge: internal teams often see their environment through a defender’s lens. Attackers think differently. They look for blind spots, unconventional paths, and overlooked weaknesses. That’s why bringing in a third-party expert is essential. External specialists provide an unbiased, attacker-centric perspective that internal teams rarely achieve on their own.
Our threat modeling services go beyond theory. Through expert-led tabletop exercises and real-world attack simulations, we stress-test your people, processes, and technology against motivated adversaries. This approach uncovers hidden vulnerabilities, strengthens defenses, and builds resilience—before an actual breach occurs.
Don’t wait for an incident to reveal your weaknesses.
Partner with us to:
- Gain insight into how attackers view your organization.
- Identify and close gaps before they’re exploited.
- Elevate your security posture with actionable intelligence.
Contact us today to schedule a consultation and take the first step toward a more secure future.
Myths About Threat Modeling—and Why They’re Wrong
-
“We already do pen tests with tools AND people … we don’t need threat modeling.”
Penetration tests show what can be exploited today, but they don’t predict what could happen tomorrow. Threat modeling identifies future attack paths before they become real vulnerabilities.
-
“The system is already built and deployed … there’s no reason to do threat modeling.”
Threats evolve. New integrations, updates, and business changes introduce fresh risks. Threat modeling is not a one-time event—it’s an ongoing process.
-
“We did a threat model when the system was built … we don’t need to do it again.”
Yesterday’s threat model doesn’t account for today’s adversaries or tomorrow’s technology. Continuous modeling ensures your defenses stay relevant.
-
“Threat modeling is too complicated.”
It doesn’t have to be. With the right framework and expert guidance, threat modeling becomes a practical, repeatable process that delivers actionable insights.
-
“We don’t have software security experts, so we can’t do threat modeling.”
That’s exactly why you need it. External specialists bring attacker-centric thinking and proven methodologies your internal team may lack.
-
“I’m doing threat modeling at all the right times … there’s no reason to do pen tests or code reviews anymore.”
Threat modeling complements—not replaces—other security practices. It helps prioritize what pen tests and code reviews should focus on, making them more effective
1. PHYSICAL
This is the lowest layer where the hardware shares the same physical, real-world space as the user. This is where we put locks on doors to keep systems safe.

2. DATA LINK
At this layer, the data is just one level above the bare metal and silicon of the hardware. Here, the data moves from software to hardware and back. Security at this layer keeps the traffic going and the data where it’s supposed to be.
3. NETWORK
Think traffic control, speed limits, detours and stop signs. This is where network addressing, routing and other traffic control take place. Security at this layer protects against flooding attacks and sniffing or snooping attacks to keep criminals from accessing logins and passwords sent over the network.

4. TRANSPORT
Think of the post office getting mail from point A to point B reliably and without anyone tampering with the contents, but instead of bills and postcards, you’re dealing with data, and instead of houses and apartments, you’re dealing with computers and networks. Denial-of-service attacks also occur here, as well as man-in-the-middle attacks (bad guys trying to intercept the data between point A and point B).

5. SESSION
This represents the continuous exchange of information in the form of multiple back-and-forth transmissions. The session layer controls the dialogues (connections) between computers. Examples of attacks are denial-of-service and spoofing.

6. PRESENTATION
The presentation layer is just below the application layer and transforms data into the form that the application accepts. For instance, feed HTML code to a web browser, and you’ll get a webpage. Give it to your phone’s texting application, and you’ll get a lot of computer text that makes no sense to your friend.

7. APPLICATION
This is the layer closest to the end user and the most troublesome these days. Commonly, web browsers and email clients are attacked at this layer. It’s how people interact with computers and devices.