PROTECTIT® - Managed Cyber Security Services
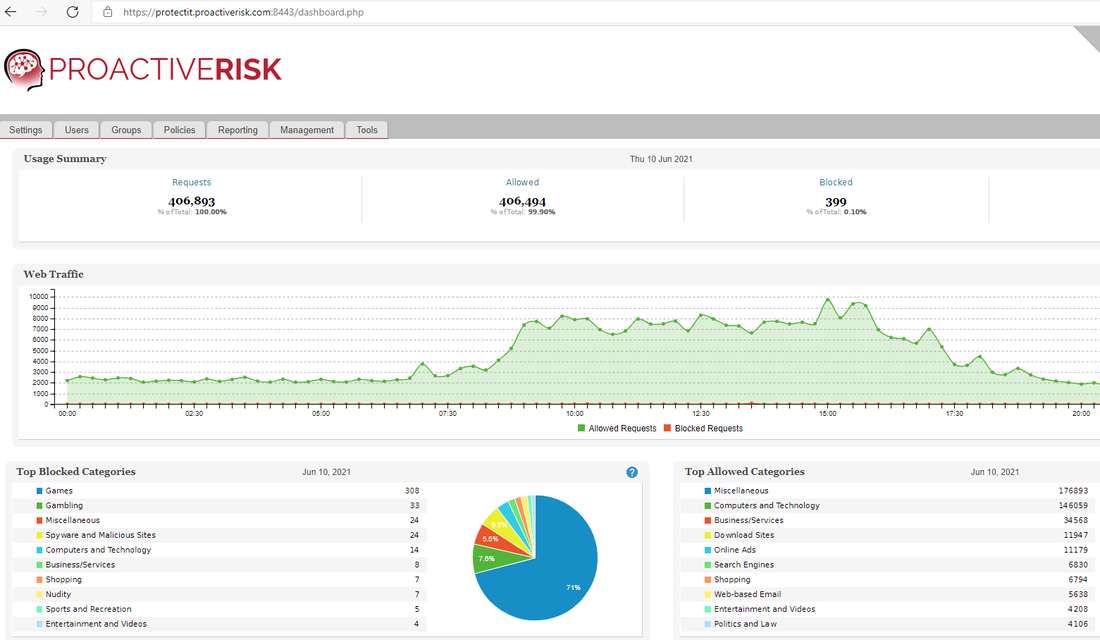
All DNS traffic from your business network is inspected and classified good/bad/other. If the traffic is destined malware infected website, a phishing site or a restricted category is it BLOCKED, alerted to the user and logged that simple.
Features and benefits
|
|