CyberEnsure operational continuity, integrity, and safety across your industrial networks and critical infrastructures with our comprehensive Information Technology (IT) and Operational Technology (OT) services. At Proactive Risk, we provide relentless monitoring of your business’s network and systems, proactively detecting signs of cyber threats.
Leverage our state-of-the-art tools and cutting-edge technologies to quickly identify, analyze, and neutralize security risks. Our integrated approach combines IT and OT security, enabling us to offer a holistic defense strategy. This proactive method ensures early detection and mitigation of potential threats, keeping them from escalating. Trust ProactiveRISK to fortify your operations with a resilient shield, maintaining the continuous safety and integrity of your technology-dependent operations Lean More >> |
InvestigationsOur state-of-the-art service simplifies the e-discovery process, empowering your team to operate with unprecedented efficiency and accuracy.
Effortless Discovery and Management: With RAPTOR, navigating through vast amounts of electronic data becomes straightforward and swift. Whether it's emails, documents, or social media content, our managed platform enables seamless search, review, and production. RAPTOR’s advanced search capabilities are engineered to pinpoint critical information swiftly and accurately, ensuring that no detail is overlooked. Your Partner in E-Discovery: Choose RAPTOR for a solution that not only meets the demands of modern e-discovery but also transforms challenges into opportunities for success in any investigative or legal environment. Engage with ProactiveRISK today. Learn More >> |
ComplianceWe specialize in navigating the intricate realm of regulatory compliance for associations and corporations. Our expertise spans across several pivotal regulatory bodies, such as the Federal Trade Commission (FTC), Environmental Protection Agency (EPA), Securities and Exchange Commission (SEC), and the Federal Financial Institutions Examination Council (FFIEC)
We don't just help your business meet compliance standards—we enable you to exceed them with confidence. Our strategies are aligned with leading frameworks, including the Center for Internet Security v8 and the NIST Cybersecurity Framework, ensuring your operations are defensible, secure and compliant. Utilizing cybersecurity as a strategic asset provides businesses with a competitive advantage by safeguarding critical assets, maintaining customer trust, and ensuring operational resilience. By proactively addressing security threats, companies can differentiate themselves in the marketplace, enhance their reputation, and create additional value through innovative, secure services. Learn More >> |
CATSCAN®CATSCAN® provides a realistic and rigorous assessment of a system's ability to withstand targeted attacks, thus offering clients a clear view of their security strengths and weaknesses.
|
VCISOEnjoy the benefits of senior-level expertise minus the cost and commitment of a full-time CISO hire. Our Senior Security Consulants have knowledge and experience with enterprise operations
|
MANAGEIT®Experience the peace of mind that comes with knowing your technology needs are in the hands of experts with MANAGEIT® with options.
|
developmentA trusted service partner of multiple commercial software programs and contributor to open-source projects. We unlock the full power of workflow automation - learn more
|
PhishingOur PhishIT® managed service educates and tests your end users through automated attack simulations, quality security awareness training, and actionable reporting metrics - learn more
|
threat modelingThe best time to review the plan is before the system is in production. We conduct deep review and tabletop threat modeling - learn more
|
We’ll conduct a discovery meeting to understand your particular business needs and challenges. Then we’ll interview your staff to appreciate their day-to-day struggles and frustrations. Next, we’ll audit your existing infrastructure, devices, applications, and workflows to determine how far from your ideal state of business performance you currently are. Finally, we’ll get to work on architecting a solution that overcomes your technology, workflow, and efficiency challenges that deliver real value and return on your investment to implement it.
Once we’ve agreed to engage, our discovery and assessment meetings can be scheduled within two weeks. Following these meetings, we’ll be able to schedule an onsite infrastructure assessment within the following week. For a typical small office location, our onsite infrastructure assessments can usually be completed in a day.
It will take us approximately a week to analyze the information gathered during the discovery meetings and the technology assessment. We’ll be able to meet with you the following week to deliver our findings and recommendations.
Once we’ve agreed to engage, our discovery and assessment meetings can be scheduled within two weeks. Following these meetings, we’ll be able to schedule an onsite infrastructure assessment within the following week. For a typical small office location, our onsite infrastructure assessments can usually be completed in a day.
It will take us approximately a week to analyze the information gathered during the discovery meetings and the technology assessment. We’ll be able to meet with you the following week to deliver our findings and recommendations.
In the fast-paced, interconnected world of critical infrastructure, you need an IT partner that doesn't just keep up, but leads the way. ProactiveRISK stands as that leader, especially within the vibrant sectors of the Northeast. Our hands-on experience and cutting-edge services provide unparalleled support where it matters most.
Founded by industry veteran Tom Brennan, ProactiveRISK stands as a beacon for organizations navigating the complexities of information assurance. With Brennan at the helm, our firm embodies a legacy of deep-seated expertise and a proven track record in protecting enterprise data. His formidable experience, gained from pivotal roles at both industry and global service providers coupled with honorable service in the United States Marine Corps, forms the bedrock of our robust security posture. Brennan's esteemed leadership extends beyond ProactiveRISK. His community contributions include over a decade with the OWASP Foundation Technical Director at SAFECode, and his ongoing role as Chairman of the Americas Board for CREST International, highlight a career dedicated to advancing cybersecurity and data protection practices. These roles accentuate his comprehensive understanding of the field—knowledge that ProactiveRISK channels into developing cutting-edge information assurance programs.
Our Commitment
At ProactiveRISK, we are committed to delivering unparalleled expertise and service. Our dedication to your business's success is reflected in our hands-on approach to managing and safeguarding your data. We don't just protect your information; we prepare you for a future where your business can thrive, unimpeded by technological threats.
Partner with Us
Embrace a future where your business's technology is an asset, not a liability. Join forces with ProactiveRISK to harness the power of top-tier cybersecurity and robust information assurance. Our expertise can become your strongest asset in the digital era.
- Wall Street's IT Vanguard: Amidst the financial heart of New York City, ProactiveRISK delivers robust IT solutions for banking and trading operations. Our expertise ensures your transactions and data flow securely and swiftly, powering the pulse of Wall Street.
- Energy Grid Maestros: With ProactiveRISK, the complex energy grids of nuclear, gas, hydroelectric, and renewable sources are managed with precision. Collaborating with industry giants like PJM and ISO New England, we help your systems operate without a glitch.
- Public Health Protectors: In critical public health sectors, ProactiveRISK’s IT solutions safeguard hospitals, research institutions, and emergency services. We equip you with the technology to save lives and maintain public well-being.
- Transportation Reliability Enhancers: We enhance the reliability of major airports, seaports, and railways, keeping the lifelines of travel and shipping robust and resilient.
- Water Supply Stewards: Our sustainable and innovative approaches keep the taps running and communities thriving.
- Law Enforcement Liaisons: ProactiveRISK extends its IT prowess to law enforcement agencies, integrating cutting-edge digital forensics, and secure communications systems that enable officers to act swiftly and informedly.
- Legal System Strategists: Understanding the intricate needs of the legal field, ProactiveRISK offers specialized IT solutions that manage case files, court records, and sensitive data with unmatched security and efficiency. Our systems ensure that legal practitioners have the tools for success in an increasingly digital courtroom
Our Commitment
At ProactiveRISK, we are committed to delivering unparalleled expertise and service. Our dedication to your business's success is reflected in our hands-on approach to managing and safeguarding your data. We don't just protect your information; we prepare you for a future where your business can thrive, unimpeded by technological threats.
Partner with Us
Embrace a future where your business's technology is an asset, not a liability. Join forces with ProactiveRISK to harness the power of top-tier cybersecurity and robust information assurance. Our expertise can become your strongest asset in the digital era.
Governance, Risk, and Compliance
|
Proactive Risk provides continuous monitoring of first-party and third-party security risks empowering clients to find, fix and remediate. We maintain a global panel of accredited service providers and manage multiple governance risk and technology platforms.
Our clients include critical infrastructure, legal, and insurance. Schedule your complimentary risk consultation today and start demonstrating commercially reasonable security. |
|
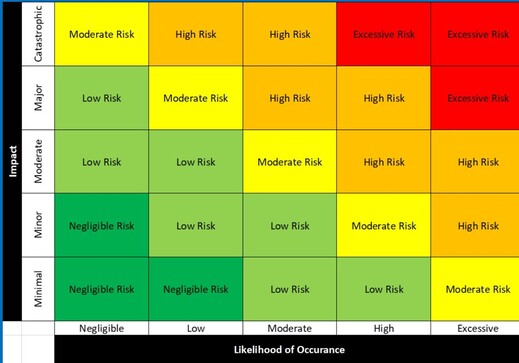
Proactive cybersecurity risk management is the process of identifying, assessing, and mitigating or eliminating the vulnerabilities and threats to an organization's information systems and networks. It involves a set of activities that are designed to protect against cyber attacks, data breaches, and other security incidents.
This can be achieved through a variety of measures, including:
|
Proactive Risk works with organizations to reduce the likelihood of adverse events occurring, minimize their impact if they do occur, and ensure that they are prepared to respond when risks do materialize.
To learn more about CATSCAN® click here
We help organizations better understand their risks ranging from tabletop exercises to technical assessments partnering with our clients to make informed decisions about how to manage technical Risk
|