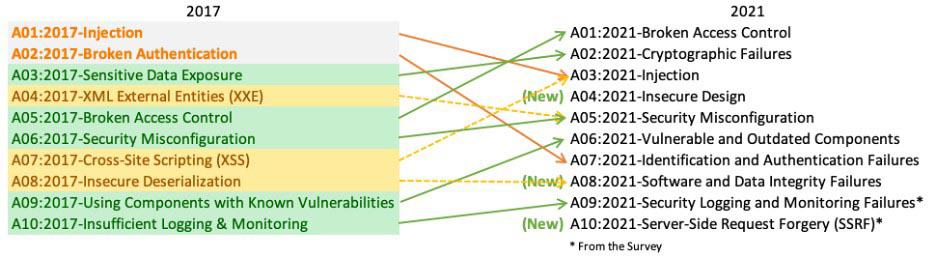
 Published in CPO Magazine April 6th 2022 Post-COVID, a growing number of mid-sized businesses are merging with and acquiring other companies to adapt, grow and expand. This process takes a tremendous amount of preparation and research. From business financials and intellectual property to contracts and tax issues, there is much to be done to help ensure a successful M&A transaction. Among top considerations during the M&A process should be your technical controls. In specific, you need to pay close attention to the software bill of materials (SBOM), and several other vital areas of your technology-enabled business. If the target organization cannot demonstrate technical maturity, it will be score lowered and may ultimately see a reduced acquiring offer or be a deal-breaker altogether. During the due diligence process, be prepared to present and describe your software-based technology product with documentation. What is expected during a technical due diligence review is architectural diagrams, scalability, and performance metrics. Technology choices made, including programming languages, databases, and infrastructure choices, will be reviewed. Your key staff must also be able to describe any software development practices and provide details on continuous deployment environments.. In particular, a review of the OWASP Top 10 2021 List is recommended. Be certain that you are able to answer questions about how you ensure code quality in a hostile internet-connected environment and perform an independent third party code audit Depending on the reason for the merger or acquisition, it could be equally important to have technical controls in place for the operations side of the business. Here it’s important to evaluate how data is processed in 17 key areas:
Remember – confidentiality, integrity and availability are important items of consideration for your technology choices from day one. Be certain to use company that has been accredited to perform valuable third-party assessments with proven policies, processes and procedures to validate your technology and environment. With a credible third-party validation of your technical maturity, you can ensure that the technical elements of your due diligence will enhance acquisition offers and simplify the integration process.
For more information, contact us on how we can help you be proactive. Comments are closed.
|
CategoriesTom BrennanThis is my blog, there are many like it but this one is mine. Enjoy. BLOG Archives
June 2024
|
|
Protecting Your Business with People, Process, and Technology
© COPYRIGHT 2024. ALL RIGHTS RESERVED. |


 RSS Feed
RSS Feed